Cyberattacks must be detected early if they are to be neutralised before major damage is done. Our Managed Detection and Response (MDR) solution combines the knowledge of a multi-disciplinary, dedicated Security Operation Center (SOC), world-class Threat Intelligence, and Security Information & Event Management (SIEM) to defend against threats.
Benefit from a solution that is tailored to suit your company and its data. Detect attacks smarter, faster and more comprehensively, with coverage of on-premises and cloud solutions from one provider.
Managed Detection and Response: The main features
Threat Intelligence (TI)
Our MDR uses market-leading threat intelligence to align your detection capability with the latest threats so they are identified and stopped before they can harm your company.
24x7x365 analysis
Our global SOC is constantly in action, monitoring and analysing activities to detect and eliminate threats and provide you with actionable insights.
Continuous optimisation
Software is never fully efficient straight out of the box. Our team fine-tunes your SIEM systems and develops custom sets of rules that reduce false positives and prioritise detection where it is needed most.
Proactive hunting
We complement the power of artificial intelligence (AI)-driven analysis with threat hunting to anticipate and detect complex threats that could slip under the radar.
How Managed Detection and Response works
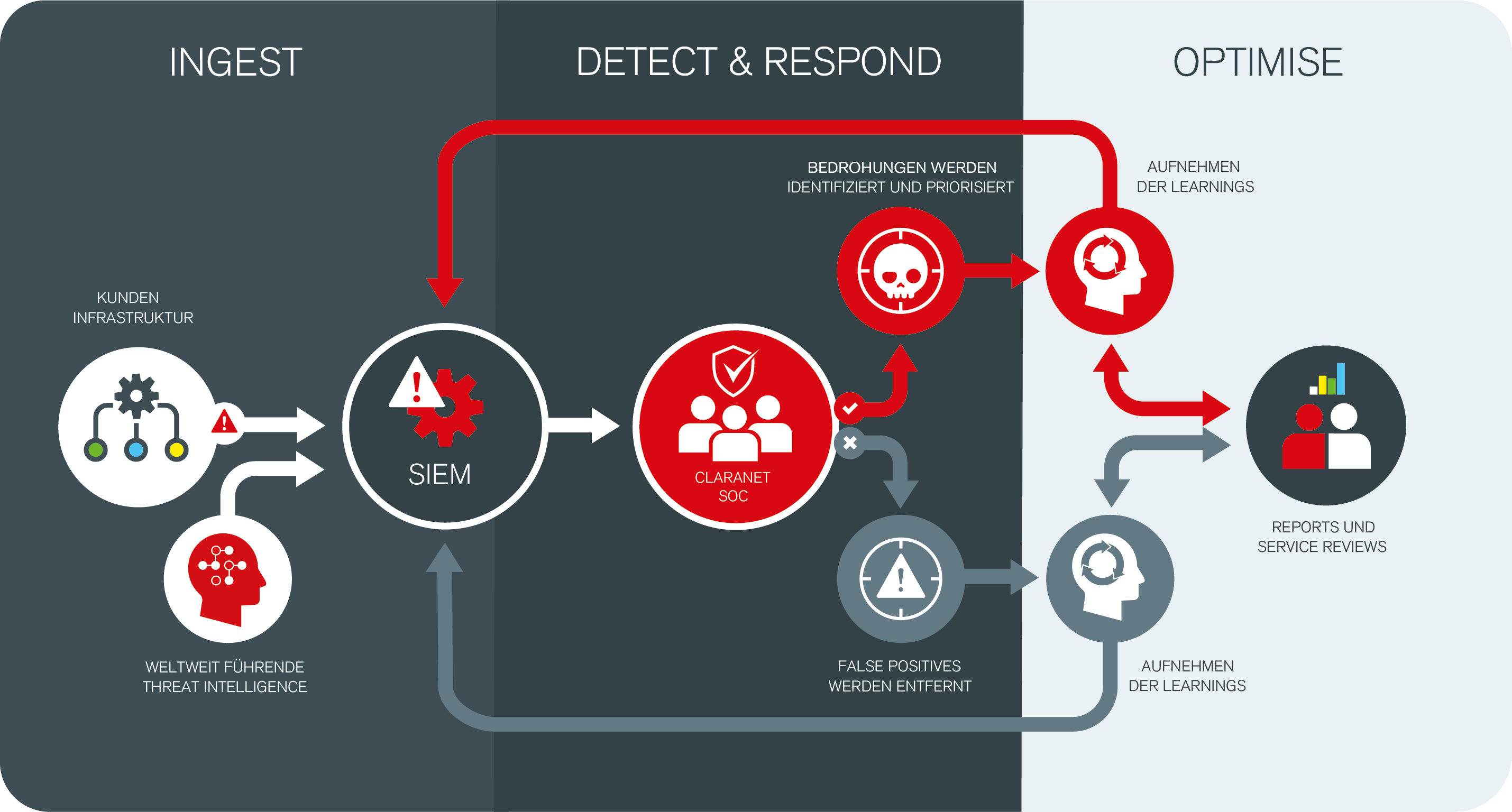
Informationsaufnahme
Security logs and alerts , generated in your infrastructure are captured by our central Security Information and Event Management (SIEM) platform, which provides a central view of your data.
Information from world-leading Threat Intelligence (TI) also feeds into the informal detection with confirmed malicious indicators of compromise (IoCs).
Erkennen und Handeln
IoCs trigger alarms and are transmitted to the Claranet SOC. False positive messages are removed.
Confirmed malicious activity is graded according to severity and escalated for elimination or deeper processing.
Threat Hunting is used to identify undetected threats and to optimise detection.
Optimieren
The insights gained are used to optimise alerts and train SIEM platforms to focus on the highest priority threats.
Regular reports and service reviews take place to further improve performance.
Accreditations within the Claranet Group

















